When I visited Cisco Studio 2021, I predicted the firewall to be history shortly in enterprise networks. Many companies have a journey into this scenario, but the roadmaps strongly present the discussion. Traditional firewall thinking is ill-suited to the cloud-native SaaS operating environment, but new challenges, such as the HTTP3 protocol, are coming.
Achilles heel is the identification of malware and ransomware from encrypted traffic.
According to a Cisco Systems study, 70% of malware used encryption to bypass protection in 2018. In 2021, 90% of malware used encryption to hide activity. In addition to the Internet (HTTPS), Microsoft LDAP, MS-RPC and SMBv3, and many other corporate network protocols run encrypted on the network. Detection is not an easy task.
A cyber security technology on the market says they perform well with encrypted traffic. When I talk to a new tech company specializing in analyzing encrypted traffic, they admit that they get a “better result” by decrypting. Anyway, more challenges are coming, but I will open the history of the fight.
Stateful Firewall and AntiVirus Gateway (the 90s)
When stateful Firewall technology (TCP session control) took over the firewall market in the 1990s, network real-time anti-malware protection was an unknown concept. With the spread of the Internet, malware has become a significant problem. Continuous cleaning of workstations in antivirus failure was costly and slow. We attempted to mitigate this problem by routing Internet / Web traffic to servers separate from the firewall for “washing” using the ICAP protocol and segmenting the network.
One of the innovations was the “transparent proxy AV bridge” developed by Willie Ositis company, which we introduced to the Finnish market in the early 2000s. Internet traffic passed through the device and removed malware. The solution was quick and easy to implement. We could not “wash” the encrypted traffic, but it was under 10% of the traffic.
Ositis was acquired in 2003 by proxy technology vendor BlueCoat. This deal resulted in a combination of BlueCoat Proxy and Proxy AV, which at least, in theory, allowed SSL decryption and better detection of malware. A significant challenge for the solution was the price. Few companies could afford to implement a stateful firewall cluster (2 devices) + BlueCoat Proxy cluster (2 devices) + Proxy AV cluster (2 devices) + 4 Ethernet LAN switches + 10 devices required for configuration and maintenance with spare devices. On top of that, email antivirus and anti-spam cluster (2 devices).
Full rack of servers and expensive software was the finest in system sales but far too expensive for 95% of Finnish companies.
Next-Generation Firewall (the early 2000s)
The solution for the market was the Fortinet ™ Fortigate ™ firewall, founded in 2000. It combined firewall, antivirus, IPS/IDS, and Web URL category filtering into a single physical device. Later came Palo Alto Networks ™ (founded in 2005) and the rest of the traditional firewall technology companies.
The term Next-Generation Firewall (NGFW) was launched by Gartner ™ in 2003/2004, although its definition has been refined several times since. In 2016, Gartner ™ noted that the term NGFW is retiring.
Next-Generation Firewall and SSL inspection (Chapter 2010)
Firewall hardware allows SSL encryption. It will significantly improve the possibilities for detecting security risks. Unfortunately, the solution is not active in many companies. I see six reasons for this:
- Configuring SSL inspection requires more effort and collaboration from the expert than staying at the default setting. Let’s go where the fence is the lowest. Licenses are billed annually, but the benefit to the customer has melted down in two decades without decryption.
- SSL inspection requires a lot of computing power, which requires more equipment investment. In addition, computing capacity is needed to identify threats. If 90% of the traffic is examined instead of 10%, the old firewall cluster will be left too small without major upgrade.
- In an Internet SD-WAN (NGFW) solution, the vendor wants to implement SSL-Inspection for each site separately. Implementing it from an expert would require 10x more effort than a centralized solution. Most decentralized capacity is empty as a pledge in the current remote and home working culture—an excellent package for the seller, not the customer.
- Decrypting and managing compatibility with a workstation browser is increasingly challenging as encryption technology evolves. The idea is “if not done for all traffic, it is not worth doing.”
- SSL-Inspection and content verification will increase the transmission delay. The user experience of the application deteriorates.
- Differences in the opinions should we do “man-in-the-middle” type of activities. Also, advanced attack methods bypass 1st, 2nd, and 3rd generation defense despite decryption.
2022 Application Speed vs. Security?
The poor response time of applications in a corporate network is why most 5FN network analysis assignments. The magnitude of the application’s transmission delay will always surprise it when it reaches 500-800 ms. (fiber / Ethernet or mobile network share of e2e latency is a fraction of the total).
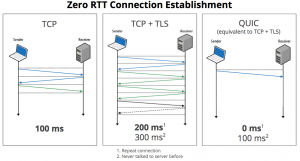
The biggest challenge is the TCP protocol developed in the 1970s, designed as a method of reliable data transmission in an unreliable data network. Cloud services are located far from the LAN. THE RESPONSE TIME BECOMES UNREASONABLY HIGH when TCP and TLS handshakes for firewalls and load balancers are added. Adding SSL inspection to the firewall increases latency and degrades the user experience.
HTTP / 3 – New and fast encrypted Internet protocol
The third version of HTTP was formerly known as HTTP-over-QUIC. It is based on the UDP (connectionless) protocol, so a slow “TCP handshake” is not required. All browsers support the protocol, and current data networks are reliable enough to use it. It can cut 50% of the response time of the application.
Use cases are real-time bidding, microservices, IoT, virtual reality, etc.
Google ™, Facebook ™, Microsoft ™, Amazon ™ use HTTP3 / QUIC to improve the user experience of services. With IETF standardization, the protocol is supported on Windows 2022 servers and many Web platforms. Unfortunately, the architecture and CPU optimization of NGFW firewalls is more or less “TCP deep packet analysis.” HTTP3 (UDP) is problematic for NGFW in performance and threat analysis. The same is true for most DDoS and SLB / WAF (Load Balancer / Web Application Firewall) products.
For now, NGFW technology vendors recommend that companies ban the HTTP3 (QUIC) protocol unless there is a compelling reason to use it. The recommendation is becoming more problematic as usage expands and people compare the user experience of a business solution as a consumer.
We need New Generation Network Security solutions in 2022
History shows that implementing cost-effective real-time network threat detection is not easy. Partly for this reason, the roadmap has moved steadily towards cloud security solutions. We want better visibility, control, and a safer solution for all user segments and IoT devices, regardless of location. A successful project achieves better data security at a lower cost. Cloud Security is an excellent option for most companies, but HTTP3 is a common challenge.
Cloud services’ scalability, performance, and rapid development have long been its strengths. Hopefully, they will solve the security challenges posed by the HTTP3 protocol, and we will also be able to enjoy fast and secure application services in companies.
Hannu Rokka, Senior Advisor
5Feet Networks Oy